Trend Security Expert
•
866 Messages
•
34.9K Points
Privacy-Enhancing Technologies: What are they and how do these protect your data?

The Internet has become our most preferred medium of communication especially during the pandemic, and as we further utilize the use of the Internet, we become more conscious about our personal data online. With that comes the rising demand for data security and privacy from consumers. Privacy regulations such as General Data Protection Regulation or GDPR and California Consumer Privacy Act or CCPA were passed to address these privacy concerns and required organizations to implement stricter data security and privacy of their consumers’ data. This also allowed consumers to have more power on how their data is being processed and managed by certain organizations.
With the existence of these Data Privacy regulations, organizations are finding ways to provide better data security for their consumers. One of the technologies they’re looking into is the Privacy-Enhancing Technologies or PETs.
What are Privacy-Enhancing Technologies (PETs)?
Privacy-Enhancing Technologies or PETs are a set of technologies (software or hardware solutions) that allows organizations to extract the value of big consumer data without compromising its security and privacy. Here are some of its examples:
It is a type of encryption that allows a system to return an encrypted result without ever requiring the dataset to be decrypted while being computed.
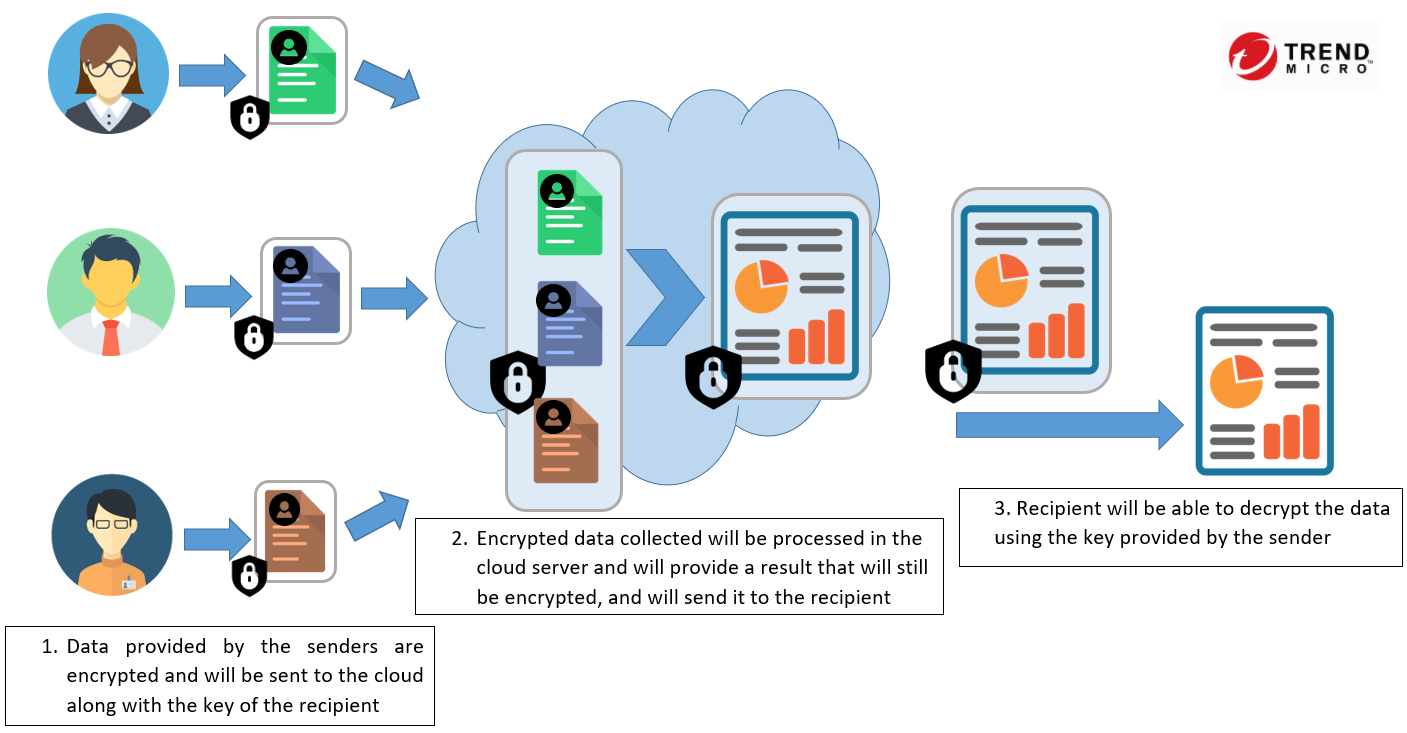
Normally, a dataset needs to be decrypted before it can be computed which is why it also allows organizations to outsource the data computation to other entities without allowing these third-parties to have access to the raw data.
How it protects your data?
Homomorphic Encryption ensures that all data will be protected from any compromises that the cloud environment may encounter. For instance, let’s say that a bank would like to host banking information on the cloud. Regardless of whether the cloud provider is hacked, the data stored will be kept encrypted, and only authorized bank employees will have access to these data.
Disadvantages of Homomorphic Encryption
Homomorphic Encryption, although considered to be the most secured PET, still provides a slow performance—making the implementation of this technology to be costly.
2. Secure Multiparty Computation (SMPC)
It enables organizations to analyze big data collaboratively without requiring them to reveal any private information. Suppose that you have a contact tracing app installed on your mobile device developed by the local government and you want to know if you are at risk to CoVID-19, using the SMPC tool, the app can provide you the results without ever revealing your sensitive data to the government.
How it protects your data?
SMPC prevents the exposure of the input data from multiple parties while the system performs a computation on the server—ensuring that all underlying data will be kept encrypted even when the server gets compromised.
Disadvantages of Secure Multiparty Encryption
The output from SMPC query is not encrypted, which means that the result dataset from the query may or may not contain sensitive information depending on what is the desired output from multiple parties.
Apart from the two technologies above, there’s also Differential Privacy, a system that allows sharing of public information while preserving the personal information of the individuals in the dataset. Another one is the Trusted Execution Environments, a trusted and isolated environment where codes and data can be executed and protected in regards to confidentiality and integrity.
And as per Ellison Anne Williams, Homomorphic Encryption is highly recommended and the one that provides the best protection among the four technologies mentioned.
These PETs are complex and powerful technologies in modern cryptography. Though all of them are similar to “privacy-preserving” technologies, they offer different approaches and can be used depending on the security requirement of the business use cases, as Christopher Hockenbrocht described in his article CRYPTOGRAPHIC TECHNIQUES AND THE PRIVACY PROBLEMS THEY SOLVE. These technologies have proved that consumers cannot just rely on privacy regulations set by governmental institutions for the security of their data, privacy organizations will also need to invest in these privacy-preserving technologies to enhance the security of their consumers’ data.
SHARE what you learn to protect your family and friends.
Trend Micro Researchers






bvasilev
Superstar
•
190 Messages
•
7.6K Points
3 years ago
1
tm_kree
Trend Security Expert
•
866 Messages
•
34.9K Points
3 years ago
Hi Team,
Don't forget to SHARE what you've learned from this article with your family and friends. Remember sharing is caring!
^Kree
0